Date: August 15, 2025
Overview
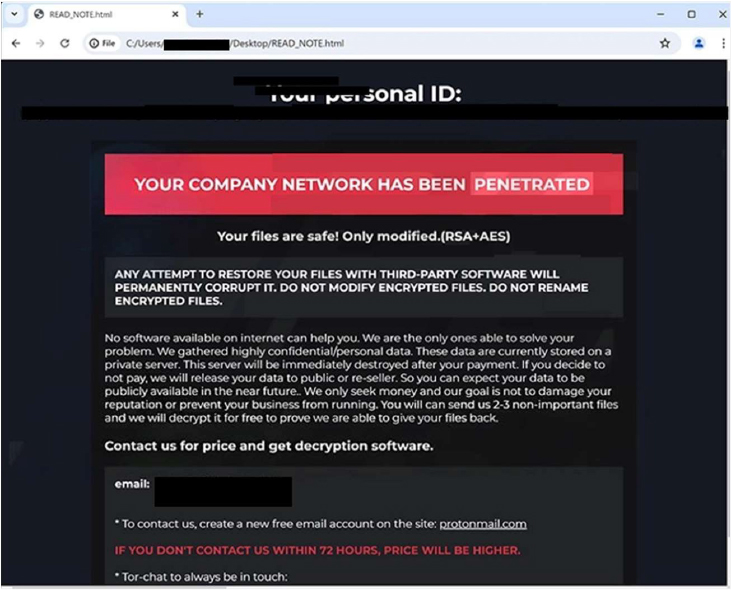
CYFIRMA researchers have identified a ransomware strain named Jackpot, part of the MedusaLocker family, now active in underground forums and targeting Windows systems. ([CYFIRMA Weekly Intelligence Report – August 15, 2025])
How It Works
- Encrypts files with RSA + AES, adding unique extensions like
.jackpot27. - Changes desktop wallpaper and drops READ_NOTE.html ransom notes.
- Victims must contact attackers within 72 hours to avoid higher ransom demands.
Attack Techniques (MITRE ATT&CK)
- Execution: scripting (T1059)
- Persistence: registry/bootkit changes (T1542, T1547)
- Privilege Escalation: access token manipulation (T1134)
- Defense Evasion: obfuscation, rootkits (T1027, T1564)
Why It Matters
Jackpot combines encryption, data theft, and psychological pressure, making it a high-impact threat—especially given its MedusaLocker heritage.
Defense Tips
- Avoid opening suspicious links/attachments.
- Maintain offline, tested backups.
- Use EDR tools to detect suspicious changes.
- Train staff to recognize and report phishing attempts.
Final Thought
Jackpot shows ransomware tactics are evolving. Swift patching, layered defenses, and readiness drills remain essential.